When sensitive information is disclosed, it can cause enormous issues for organizations, governments, and individuals. Hackers can exploit the internet, Bluetooth, text messaging, or the online services you use to gain access to you, whether you are offline or online. If not addressed appropriately, a little defect can result in a significant data leak. Many people do not pay enough attention to contemporary security issues because they are unaware of how prevalent they are. So, how can you protect yourself against data breaches?
We’ll go through data breaches and how they might affect you in this post.
In this article, you will find solutions to questions such as What are data breaches? What causes a data breach? How can a data breach affect you? How do you prevent data breaches?
Before anything, we’ll start off by data breach definition.
What is a data breach?
So what is a data breach? Well, basically, a data breach happens when sensitive, confidential, or protected information gets exposed to an unauthorized individual or group. In a data breach, files are seen and/or shared without authorization.
A situation as such can affect anybody, including individuals, small companies, big corporations, and governments. If the data they store is not well protected, there is a huge risk of a data breach.
Let’s look at the most common reasons why data breaches occur. They can occur due to an issue with:
- Technological faults
- User Action
With mobile devices and computers becoming more and more connected, there are more channels for data to flow through. IoT devices demonstrate that we are increasingly prioritizing convenience over security.
Many “smart home” products have serious flaws, such as a lack of encryption, and hackers are exploiting them.
This problem will worsen as new digital products, services, and tools are introduced with little security testing.
Even if the backend technology is flawless, some users will almost certainly have poor digital habits. A website or network can be compromised by just one person.
If there is not enough security at both the user and enterprise levels, there is a huge risk of a data breach.
Now that you know the risk factors related to data breaches, let’s discuss how exactly a data breach happens.
How do data breaches happen?
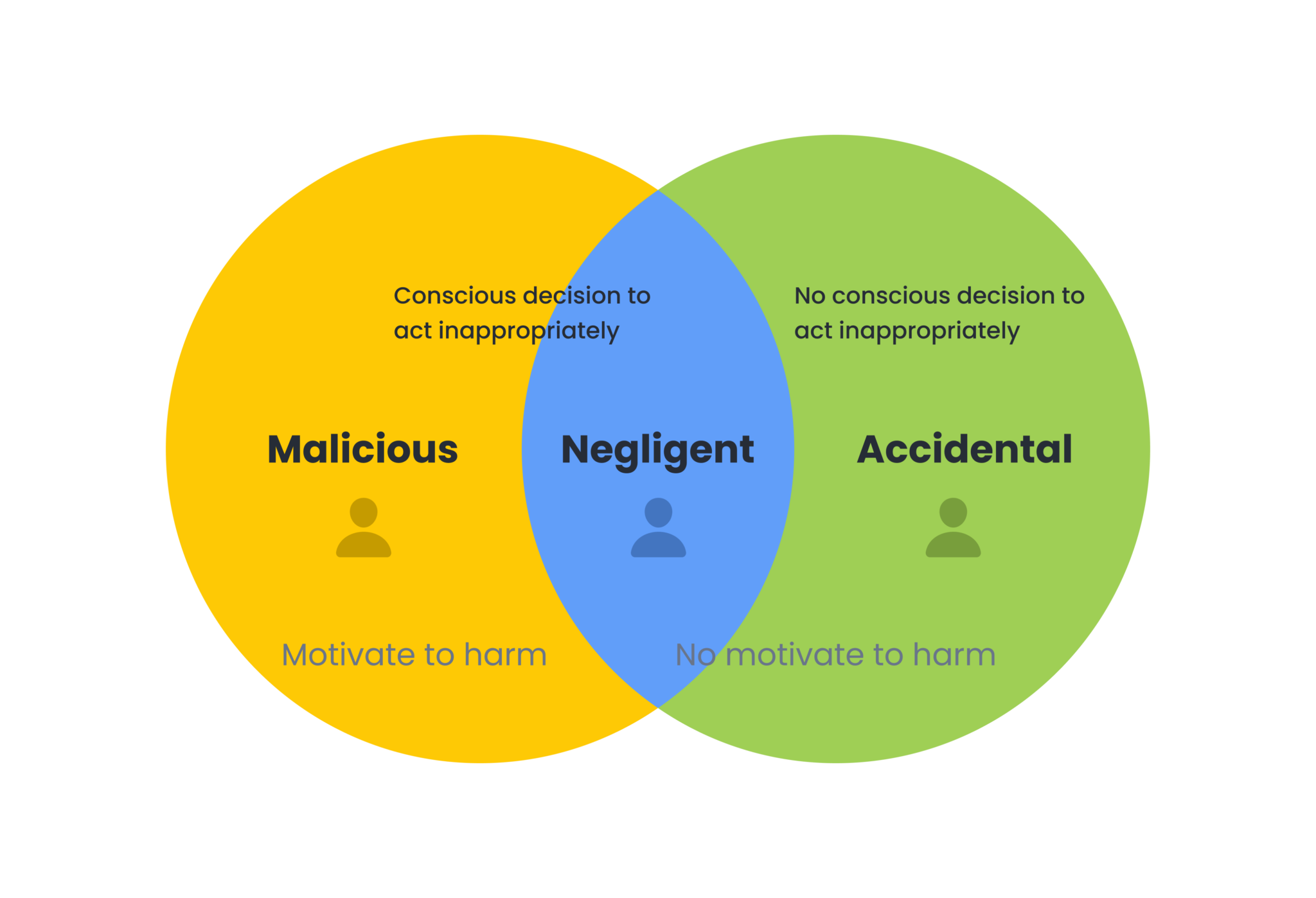
Before getting to know how you can protect yourself against data breaches, let’s understand the basics. Usually, people assume a data breach is only caused by an outside hacker. That is not always the case, though. Sometimes it can be caused by intentional, malicious attacks. However, it can just as easily be caused by a simple oversight by employees or issues in an organization’s infrastructure.
Let’s take a look at more ways a data breach can occur:
1. Malicious Insiders
An example of this scenario is when someone accesses and/or shares files deliberately to cause harm to a company or an individual. In this case, the malicious insider may have legitimate authorization to use the data. For example, he could be an employee of the same company. However, the intent is to misuse it maliciously.
2. Accidental Insiders
An accidental insider refers to someone who is an employee at a company and goes through data on a coworker’s computer without obtaining authorization permissions. Here, the access is accidental, and no information is disclosed. Here, the intent is not malicious. The data, however, is considered compromised because an unauthorized person viewed it.
3. Misplaced/stolen devices
A laptop or external hard drive containing sensitive information that is not encrypted or locked is stolen.
4. Malicious outside criminals
These hackers collect data from a network or an individual using a variety of attack vectors.
What are the malicious methods used to breach data?
Because malicious data breaches are the result of cyberattacks, you should be aware of what to look out for. Here are some popular hacking techniques:
1. Protect yourself against data breaches: Phishing
These social engineering attacks are intended to dupe you into allowing a data breach to occur. Phishing attacks usually pose as organizations or individuals they know to deceive people. Criminals of this type will try to persuade you to hand over sensitive data or provide the data itself.
2. Force attacks
Force attacks work through all of the password possibilities until they guess correctly. These attacks take time but have become more rapid as computer speeds have increased. To expedite the process, hackers may infect other devices, including yours, with malware. If your password is weak, cracking it may only take a few seconds.
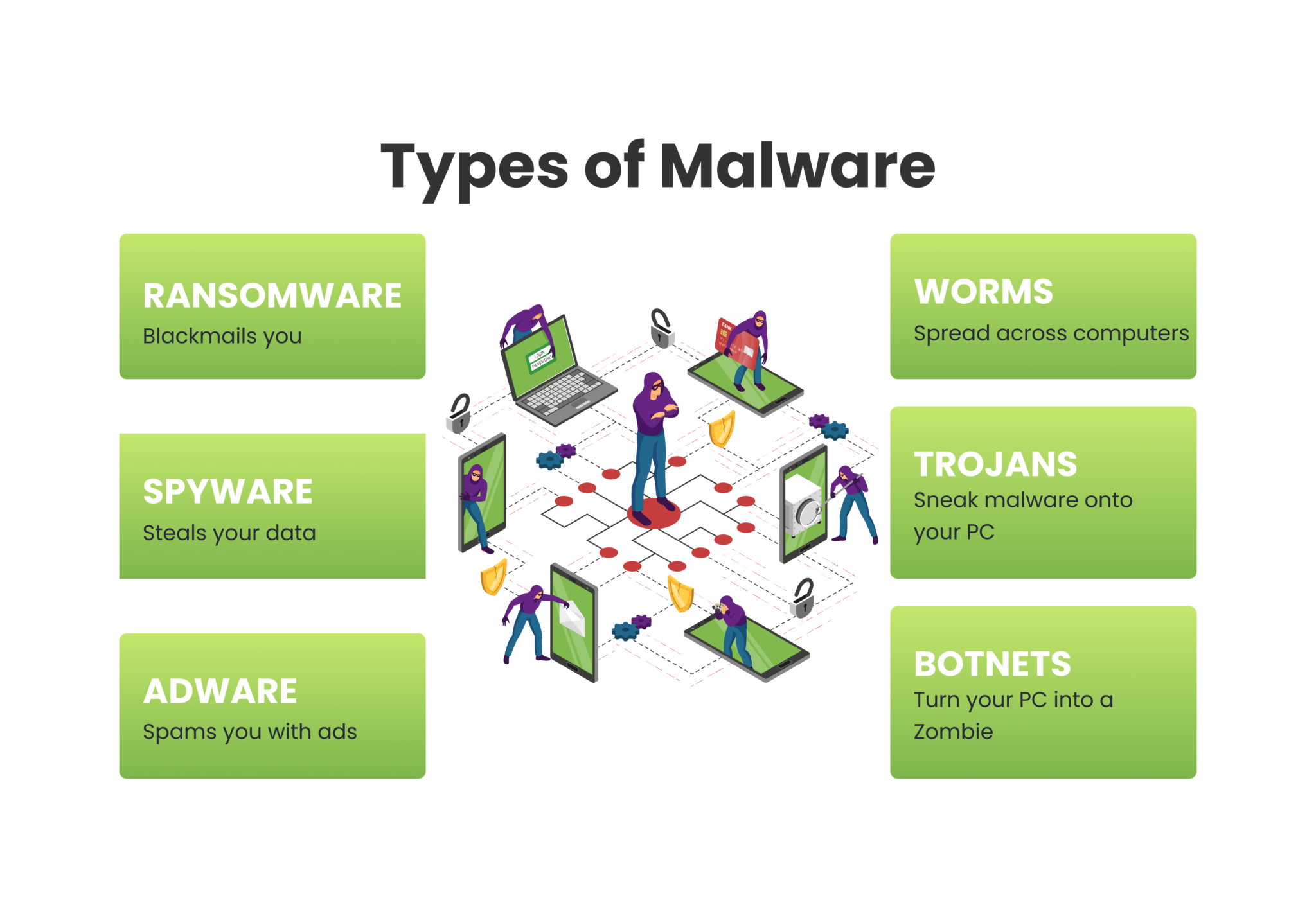
3. Malware
The operating system, software, and hardware on your device, as well as the network and servers to which you are connected, may have security flaws. Criminals look for these gaps in security as the ideal place to inject malware. Spyware, in particular, is ideal for stealing private information while remaining completely undetected. This infection may not be discovered until it is too late.
What are the common targets of data breaches?
Your comprehension of this subject is vital to protecting yourself against data breaches. A data breach might occur due to an unintentional error or by a hacker with malice intent. Either way, actual harm can occur in these situations. This can happen when the individual with unauthorized access obtains and shares Personally Identifiable Information (PII) or company intellectual information. Their reasons for doing so can be malice, financial gain, or both.
Malicious criminals follow a simple pattern: targeting an organization for a breach requires advance planning. First, they would learn about their victims. This helps them figure out weaknesses or faults like missing or failed upgrades and staff vulnerabilities.
Malicious hackers figure out their targets’ weaknesses. Then they come up with a plan to trick insiders into downloading malware.
Once accessed, hackers can search for the data they want, and they have time to do so. That is because an average breach can take over five months to be detected.
There are common vulnerabilities targeted by malicious hackers. They include the following:
1. Weak credentials
The vast majority of data breaches are the result of stolen or compromised credentials. If malicious criminals have your username and password, they have access to your network. This can happen when people reuse their passwords. Hackers can use brute force attacks to obtain access to websites, email, bank accounts, and more sources of personal data, including your financial details.
2. Compromised assets
Malware attacks of various types are used to negate regular authentication steps that would normally protect a computer.
3. Stolen credentials
Phishing-related security breaches are a major concern, and if cyber criminals obtain this personal information, they can use it to access things like your bank and online accounts.
4. Payment Card Fraud
Card skimmers are devices that attach to gas stations or ATMs and take data when a card is swiped.
5. Access from a third party
You may try your best to keep your data and network as secure as possible. However, hackers may still exploit third-party providers to get access to the system.
6. Mobile phones
Are your employees allowed to bring their own devices (BYOD) to work? If yes, you have to reconsider that decision. Remember that insecure devices may download malware-laden programs that enable hackers to gain access to information saved on the device. This frequently contains work email and files, as well as personally identifiable information about the owner.
Why is a data breach dangerous?
Usually, you can’t defuse a situation involving a data breach by simply changing passwords. It is possible for a data leak to have much bigger and longer-term consequences for your finances, reputation, future plans and projects, and other assets. A data breach may be disastrous to a company’s reputation as well as its bottom line.
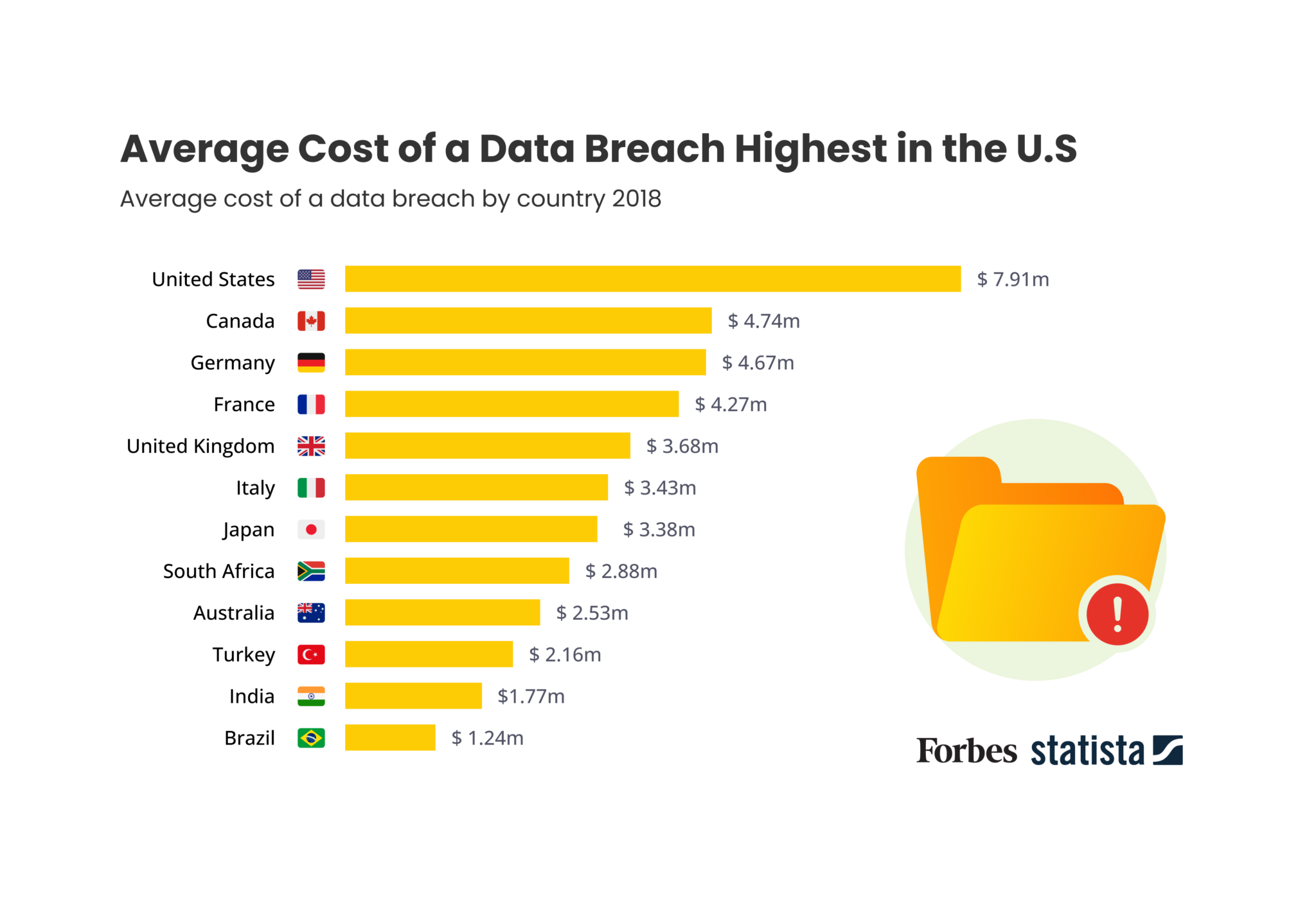
Equifax, Target, and Yahoo, for example, have all suffered from data breaches. And many people now associate or remember those companies for the data breach incident rather than their actual business operations. So, it’s critical that you protect yourself against data breaches.
1. For government agencies
Compromised data can mean exposing sensitive information to foreign parties. Military operations, political dealings, and information about critical national infrastructure can all pose a significant threat to a government and its citizens.
2. For individuals
Identity theft poses a significant risk to data breach victims. Leaks of data may expose anything from social security numbers to financial details. Once a criminal obtains your information, they may commit any sort of fraud in your name. Identity theft may wreck your credit and get you in legal trouble, and it is tough to fight back.
While these are frequent scenarios, the damage caused by data breaches can go well beyond them. As a result, it is critical that you examine whether your data has already been compromised.
More comprehensive monitoring can come in handy to let you know in real-time if there’s a data breach. It’s important to get help from products that offer data leak detection to navigate the situation.
The best solution is to be proactive. The best way to protect your data against malicious hackers is to minimize the risk of getting attacked as much as possible. In other words, a security plan is the way to go. Let’s take a look at some of the ways that you can use them to prevent data breach attacks.
How do you protect yourself against data breaches?
Data breach prevention must engage everyone at all levels, from end users to IT employees and everyone in between.
Security is just as good as its weakest link when it comes to avoiding data breaches or leaks. Every person who comes into contact with a system has the potential to be vulnerable. Even small kids with a tablet connected to your home network could pose a risk.
Things you can do to protect yourself from a data breach:
1. Protect yourself against identity theft
CNET reports that in 83% of U.S. data breaches in 2021, sensitive personal information was compromised. Contact your credit card issuers and put a fraud alert on your accounts if you fall victim to identity theft. Then, contact your regional Social Security Administration office or relevant local authorities to find out what to do next.
2. Create a notification system for your account
You may set up alerts to reach you when a specified sum of money is spent or when a transaction seems questionable. This might be an early warning that your account has been compromised.
3. Update software
Updates to your tablet, phone, router, and other devices’ software (including antivirus) are something you should think about performing often. Newer software releases often include bug fixes and other security measures to guard against hacking and other forms of cybercrime.
4. Establish strong passwords
Always use a unique password for each account. Immediately update all of them if a service you’ve recently used is compromised.
When possible, log in using a combination of credentials. This requires the presentation of two or more authentication factors before granting access. This may include a password and a code delivered to the user through phone, text message, or email.
5. Make purchases using a credit card
For unauthorized credit card purchases, your responsibility may be lower. However, if your debit account is compromised, you may be liable for charges totaling more than $500.
6. Protect yourself against data breaches: Keep an eye out for scams
If you get a warning about a data breach, call the organization to make sure it’s not a hoax. However, don’t call the number that may be provided on the notice. Instead, use a number that you know is active to make the call.

Wrapping up
In this article, we discussed all about data breaches, including what causes a data breach. How does a data breach affect you? And measures you can take to prevent data breaches. As we mentioned, a data breach can happen in numerous ways. When it does, it can cause huge issues for organizations, governments, and individuals.
If you are not taking proper precautions, you and your company are at risk of a data leak. So make sure to take the steps we discussed to keep your data protected from hackers.