To put it simply, every app-developing company must prioritize mobile app security in 2024. Yes, in today’s digital world, protecting personal and company data relies heavily on the security of mobile apps. Knowing and performing effective mobile app security procedures is of the utmost importance due to the growing dependence on these applications for everyday tasks.
OWASP mobile updates
Ranking the most pressing threats to mobile security is something that the Open Web Application Security Project (OWASP) does on a regular basis. Significant changes in 2023 mirror the dynamic nature of mobile app security. Current threats include the following:
- Misusing User Credentials: A recent update highlights the significance of strong authentication techniques and the dangers of improperly managing user credentials.
- Insufficient Supply Chain Security: This threat emphasizes the need to secure the whole mobile development lifecycle, beginning with development and ending with distribution.
- Risky Authorization and Authentication: Updated from previous years, this consolidated category offers a comprehensive approach to user access management.
Changes in emphasis are evident when comparing the 2023 list to its predecessors, including 2016 and 2014. Secure communication, for example, is no longer a primary worry. Nevertheless, inadequate encryption is still a major problem. This reorganization of focus indicates a trend in the business world toward more all-encompassing approaches to protecting mobile apps from security risks.
Mobile app security in 2024: strategies to protect sensitive data
With so much personal and business-related data kept on mobile devices in 2024, data security is going to be a major concern. In order to avoid breaches and illegal access, it is crucial to implement strong data security measures.
- Data Classification
Data classification according to sensitivity and access needs is the first stage. Because of this, it is easier to apply suitable security measures to various forms of data.
- Server storage of sensitive data
Instead of keeping sensitive data on the device itself, save it on secure servers. This method lessens the possibility of a data breach due to theft or hacking.
- Api Utilization for File Encryption
An essential tool for data protection is encryption. File encryption APIs ensure secure data transmission and storage. No one else will be able to read the data thanks to this.
- Authentication using biometrics
When it comes to accessing sensitive data, using biometric features like fingerprints and face recognition gives an extra degree of protection.
- Multi-Factor Authentication (MFA)
Multiple-factor authentication (MFA) greatly improves safety since it uses a mix of passwords, biometric checks, and location-based authentication.
- Security with artificial intelligence and machine learning
Data protection may become more dynamic and adaptable with the help of artificial intelligence and machine learning, which can proactively identify and prevent security risks.
You may successfully safeguard sensitive data on mobile devices from the increasing digital dangers by integrating these measures in 2024.
Password security management on mobile devices
There are serious dangers, such as data breaches and illegal access, associated with mobile device password management that is inadequate. Password security is becoming more important in 2024 as the use of mobile devices continues to grow.
Recommended Methods for Managing Passwords:
- Passwords that are strong and unique
Promote the use of complex, hard-to-guess passwords. To prevent unauthorized access from occurring across accounts, each one needs its own password.
- Changes to passwords on a regular basis
To reduce the likelihood of password disclosure or theft, institute procedures mandating frequent password upgrades.
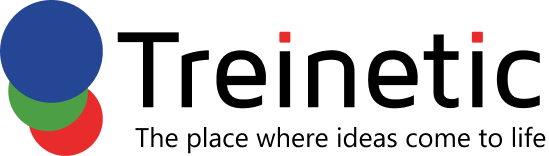
- Two-Factor Authentication (2FA)
For further protection, use two-factor authentication (2FA). Something the user knows (such as a password) and something the user has (such as a mobile device) are usually required for this.
- Password Managers
Use a safe password manager to keep track of all your passwords. Instead of having to remember a bunch of different passwords, you can use these tools to create and save complicated ones.
- Educating Users
Make sure users know the dangers of reusing passwords and the significance of using strong ones by holding frequent training sessions.
- Authentication using biometrics
Wherever possible, use biometric authentication methods like fingerprint or face recognition as an alternative to weak passwords.
- Encryption
To make saved credentials and passwords unintelligible in the event of data interception, encrypt them.
Ensuring the security of both personal and corporate data, these methods may greatly reduce potential risks linked to inadequate password management on mobile devices.
Sensitive data protection in transit
Potential security breaches abound in the digital world of mobile apps throughout the data transfer process, which begins on the user’s device and ends on the server. Protecting the data from unauthorized parties’ interception or manipulation is the main obstacle in this transit. Secure Socket Layer (SSL) and Transport Layer Security (TLS), as well as encryption, become crucial in this context.
The first level of protection is encryption, which changes sensitive data into an unreadable coded format. The danger of eavesdropping is great when sending data over public networks; thus, this is very important. By establishing an encrypted tunnel between the user’s device and the server, SSL/TLS protocols enhance this security. No matter how sensitive the data is, it will go safely and undamaged via this tunnel.
Still, you have to be careful when you put these tech ideas into action. Regularly updating your SSL/TLS setup is the best defense against ever-changing threats. Careful management of certificates is essential to avoid their abuse or expiration. Especially when sending sensitive financial or personal information, developers should make sure their apps always use these secure connections.
Users’ faith in mobile apps rests on the technological need to guarantee data security while in transit. Developers of apps may greatly reduce the dangers of data transfer by using strong encryption and secure connection protocols, giving their consumers peace of mind.
User Authentication, Authorization, and Session Management
If we want our mobile apps to be safe, we need strong authentication and session management. Their primary function is to prevent data breaches and illegal access. Correct implementation of these components ensures that only authorized users can access sensitive data and features in an app.
Methods and Recommended Approaches:
- Multi-Factor Authentication (MFA)
Make security better by using multi-factor authentication. It entails merging not one but two separate forms of authentication, such as a password, a security token, and biometric verification, all of which the user has.
- Authentication using biometrics
For safer and more convenient identification, employ biometrics such as fingerprints or face recognition.
- Breaks in the Session
Minimize the danger of illegal access, particularly on unattended devices, by enforcing automated session timeouts.
- Token-based Authentication
For the purpose of preserving session states, use token-based authentication, such as JSON Web Tokens (JWT). Since this approach does not require the server to save session data, it is more secure.
- Scheduled security assessments
To keep up with ever-evolving security threats, assess your authentication and session management procedures often and make any necessary adjustments.
- Instructions for End Users
Encourage users to always log out of their accounts, particularly when using shared devices, and to use strong passwords.
- Protecting IDs and passwords
Encrypting user credentials before sending or storing them may prevent their interception or unauthorized access.
When it comes to user authentication, authorization, and session management, mobile apps may greatly improve their security by using these strategies and best practices.
Securing platforms and backend APIs for mobile apps
Mobile applications rely on backend systems to process data, store it, and provide general functionality. Nevertheless, cybercriminals often target these systems, which puts users at risk of data breaches, illegal access, and interrupted services.
Platform and API security: API security protocols
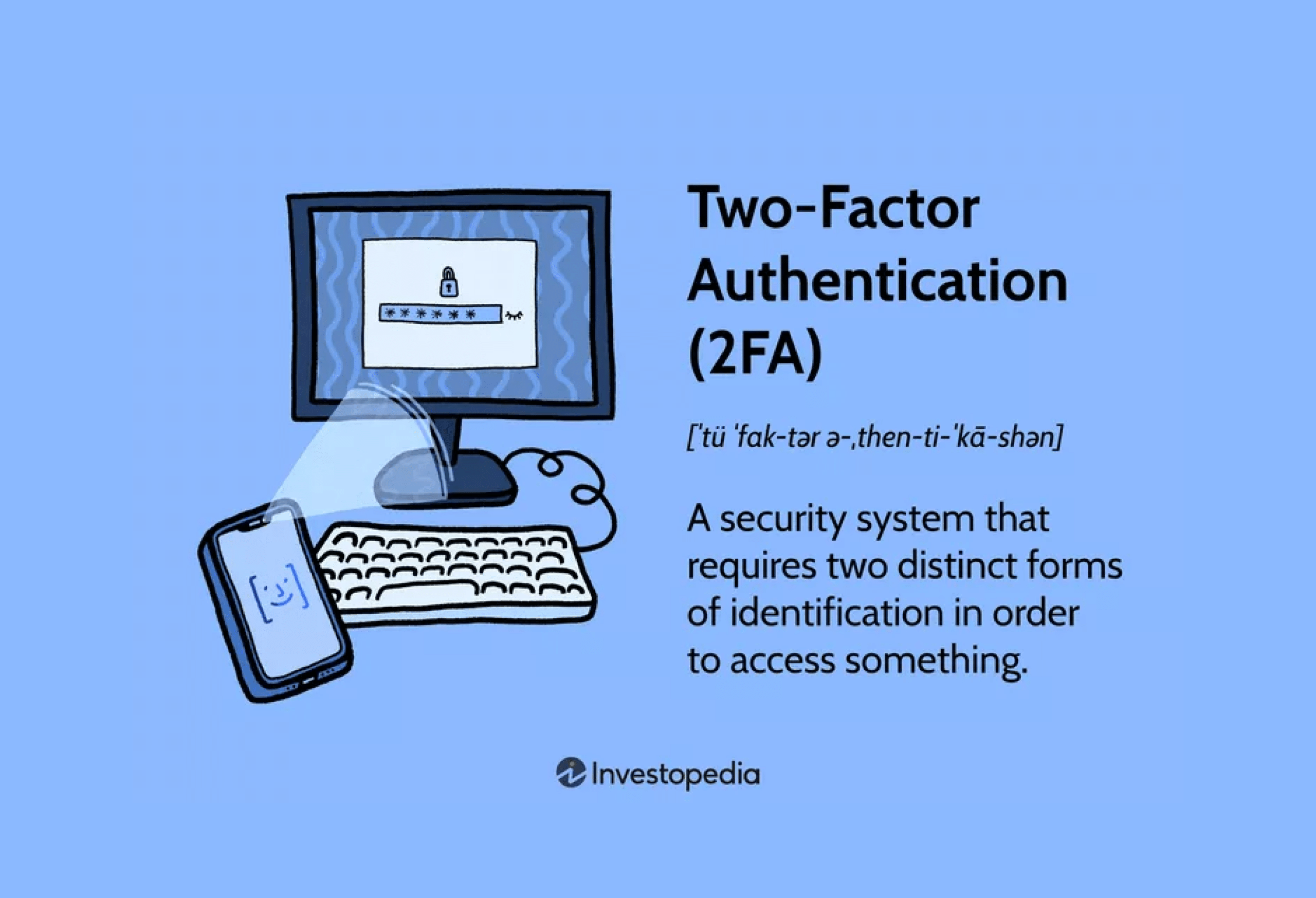
To ensure the safety of mobile applications’ backend systems, API security standards, especially OAuth2, are crucial. Applications may get restricted access to user accounts on HTTP services using OAuth2, an authorization mechanism. The system is able to access resources on the user’s behalf by means of tokens rather than credentials. For the purpose of protecting API endpoints, this protocol is quite successful, as it:
- Separates Roles
In OAuth2, the client, the authorization server, and the resource server all play separate but complementary roles. By limiting the visibility of credentials, this division strengthens security.
- Limited Access
With OAuth2, applications may employ scoped access, which means they can only access the user-granted rights rather than gaining full control of the user’s account.
- Token Expiration
Unfortunately, OAuth2’s access tokens don’t last very long. Doing so reduces the risk of access token compromise.
- Refresh Tokens
To offer a layer of convenience without sacrificing security, OAuth2 employs refresh tokens for prolonged sessions. These tokens may automatically receive new access tokens.
- Flexibility for Developers
OAuth2 is a flexible option for diverse API security requirements since it supports a wide range of application types, including web and mobile applications, server backdrops, and more.
Scheduled security assessments
Backend systems in mobile applications must undergo regular security assessments to ensure their integrity and security. In order to identify security flaws and non-compliance with regulations, these audits thoroughly check the security configuration. The following are important parts of these audits:
- Assessment of Vulnerability
Finding potential security holes in the system, such as bugs, incorrectly set up servers, or out-of-date software.
- Penetration Testing
Cyberattack simulations are used to find vulnerabilities and evaluate system resistance.
- Code Review
Examination of application source code for security vulnerabilities and compliance with recommended coding practices.
- Evaluating Compliance
Keeping the system in line with all applicable privacy and data protection laws and regulations.
- Assessing Potential Risks
Prioritizing fixes according to risk levels after evaluating the possible effects of discovered vulnerabilities.
Conducting security audits on a regular basis allows for the proactive detection and resolution of security concerns, guaranteeing the continuous protection of mobile application backend systems.
Data Encryption
An essential security technique for safeguarding sensitive data linked to mobile applications is data encryption, which applies both during transmission and storage. Take a closer look at its use case:
- Encryption in Transit
The process entails encrypting data as it travels from the mobile app to the server. To avoid data interception and eavesdropping, we employ technologies such as SSL/TLS to establish a secure link.
- Encryption at Rest
Data encrypted on servers or in the app itself is what this term refers to. Because of this, you may be certain that your data will be unreadable and inaccessible in the case of a data storage intrusion.
Apps for mobile devices may keep users’ private information safe from prying eyes by encrypting it while it’s in use and while it’s in transit.
Access Control
To guarantee that only approved users and processes may access certain resources, access control is essential in backend systems. Various mechanisms are involved in this:
- User Authentication
The practice of checking a user’s credentials (by passwords, biometrics, or multi-factor authentication) before letting them in.
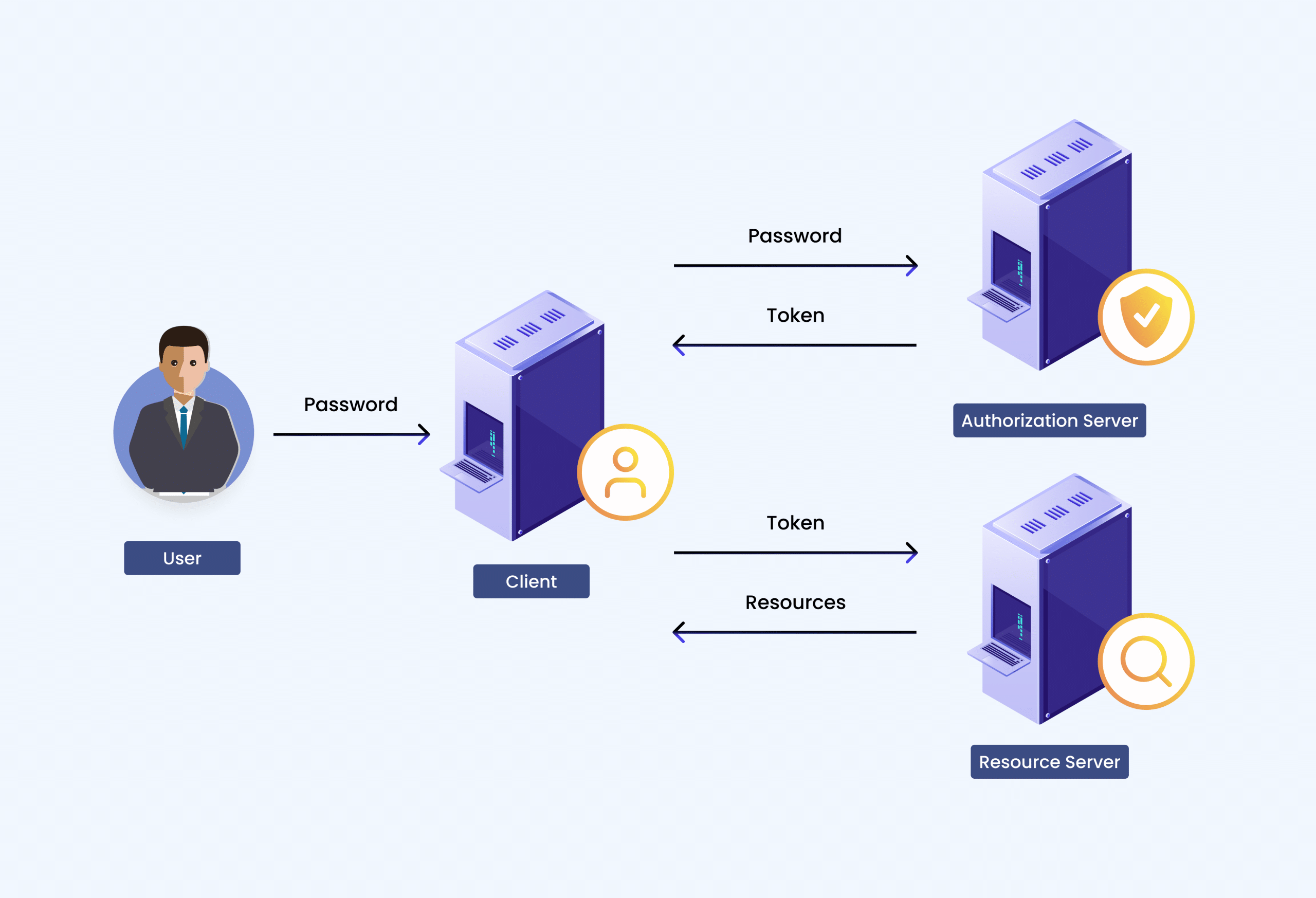
- Role-Based Access Control (RBAC)
To limit users’ access to just the resources they need to do their jobs, organizations are increasingly using role-based permissioning.
- Least Privilege Principle
Keeping sensitive information safe from prying eyes is possible by granting people only the permissions they need to do their jobs.
- Audit Trails
The ability to track who accessed what and when is critical for keeping tabs on security problems and conducting investigations.
Throttling and rate-limiting
Important security precautions for APIs include rate-limiting and throttling. To avoid overload and misuse, like denial-of-service (DoS) attacks, these methods limit the number of API requests that users may make during a certain time period. Rate limitation safeguards API availability and responsiveness for all users by establishing a cap on the total number of requests. Another similar idea is throttling, which makes the rate limit constantly adjustable depending on server load or user behavior. This makes the API even more stable and reliable when it comes to assaults or spikes in traffic. If you care about the stability and reliability of your mobile apps’ backend infrastructure, you must implement these precautions.
Monitoring and logging
Ensuring the security and integrity of mobile apps requires continuous monitoring and logging of backend systems. As part of this procedure, we keep tabs on all the transactions and activities that take place in the backend system. This allows businesses to:
- See Unusual Behavior
Determine whether there are any suspicious trends or actions that could point to an attempted security compromise.
- Audit Trails
Forensic investigations in the case of security events and compliance audits rely on auditing logs.
- Updates in Real Time
Set up systems that notify you of any security risks in real-time so you can respond and eliminate them right away.
- Analysis of Performance
Make sure the system is running well, and find ways to make it even better by monitoring its performance.
Improving mobile app security is as simple as implementing efficient monitoring and recording measures, which in turn allow for faster threat detection and response.
Mobile applications may protect themselves from various cyber risks by using these procedures, which greatly improve the security of their backend APIs and platforms.
Robust Third-Party Service Integration
While integrating third-party services into mobile applications might improve their usefulness, it also opens the door to potential security issues, including data breaches and illegal access. To mitigate the potential impact of these risks:
- Vet Third-Party Services
Find out how secure third-party services are by looking at their certifications, if they follow data protection rules, and whether there have been any data breaches in the past. See what other people have to say about their data security practices by reading reviews and comments.
- Use secure APIs
Make sure that third-party APIs utilize strong authentication mechanisms such as OAuth2 and use encryption protocols for data transport, such as SSL/TLS. The information that travels from your app to the third-party service will be more protected in this way.
- Limit Data Access
Place stringent restrictions on who may access the data. The data that third-party services may access should be clearly defined in policies, so that they can only access the data that is essential for them to perform their role. Lessening the likelihood of data disclosure is the goal of the least privilege principle.
- Make sure you continuously examine and update integrations
Monitor the third-party service integrations and ensure frequent updates. It is important to keep yourself updated on the most recent security patches and updates offered by these providers. Maintaining the safety of the integrated services requires constant vigilance in the form of audits and reviews to spot any changes to security rules or newly discovered vulnerabilities.
Gathering and Preserving User Assent
In order to comply with legal and ethical requirements while collecting data, it is essential to obtain and store user permission.
- Adherence to Law
Follow rules that require explicit user permission for data collection and use, such as the CCPA and GDPR. Verify that the permission process in your app complies with all applicable laws.
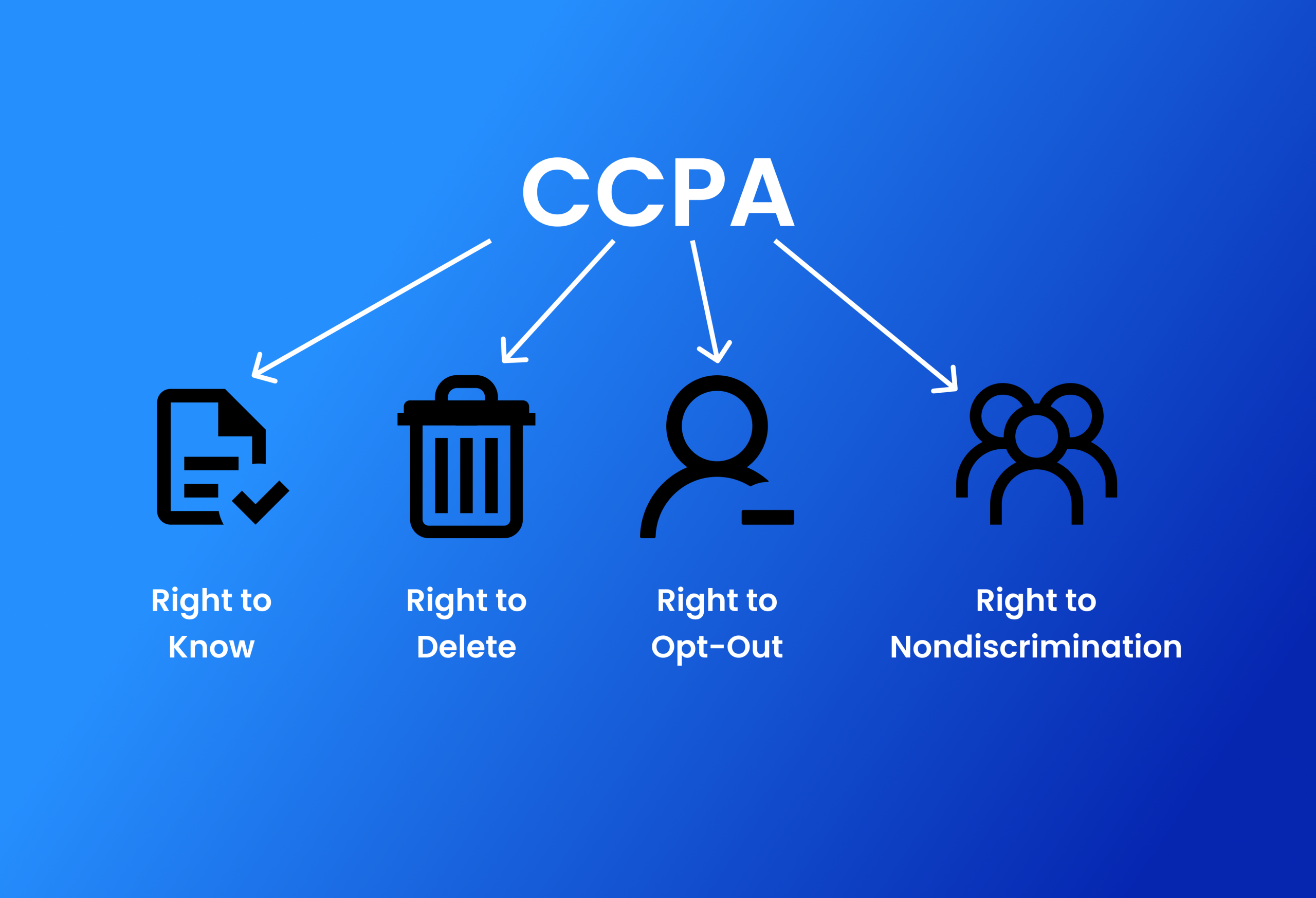
- Transparency
Make the purpose and nature of data collection and its intended use very obvious to consumers.
- Easy Opt-Out
Make it easy for users to revoke their permission whenever they choose, so they can keep their privacy protected.
- Secure Storage
Preserve a paper trail for auditing and compliance by keeping consent records in a safe and easily accessible location.
Keeping paid resources secure from unwanted access
The loss of income and the erosion of user confidence may result from unauthorized access to paid resources in mobile applications.
- A solid permission and authentication system
To make sure the verification procedure is strong, use multi-factor authentication (MFA). Multiple layers of protection, such as biometric verification, security tokens, and passwords, may be necessary. Define and enforce access privileges for premium features using fine-grained authorization restrictions.
- Managing license keys
Create a safe method of issuing and verifying digital tokens or license keys. Each user’s account should be associated with their own set of generated keys, making it impossible to share or misuse them. Set up systems to identify compromised keys and disable them.
- Ongoing evaluations and supervision
Set up a system to constantly watch for unusual activity that might indicate someone is trying to get in without permission. Make sure your access control procedures are up-to-date and effective against new threats by conducting frequent security assessments.
The Safe Handling of Mobile Application Distribution and Provisioning
To avoid virus dissemination and unauthorized alterations, it is crucial to secure the distribution and provisioning of mobile applications.
- The safety of the App Store is a priority
The official app stores, such as Google Play or Apple’s App Store, do thorough security checks, such as code analysis and virus scanning, making them an essential channel for mobile app distribution. This lessens the likelihood of distributing applications with vulnerabilities or viruses by assuring consumers that the software is safe to use.
- Signatures and Certifications in the Digital Age
To include digital signatures, you’ll need to sign your applications using a developer-specific cryptographic key. This safeguards the software against tampering by verifying that any updates or new versions come straight from the developer. Certifications add weight to the developer’s credibility.
- Encrypted Communication Channels
It is critical to use safe, encrypted communication routes, like HTTPS, while sending app updates. Encryption safeguards the program’s integrity throughout distribution by preventing attackers from intercepting and altering data, including new app versions or fixes.
Runtime Code Interpretation and Security
Security issues, such as injection attacks or unauthorized code execution, may arise from runtime code interpretation in mobile applications.
- Input Validation
Strengthen methods for validating inputs. Avoid injection vulnerabilities by implementing rigorous validation on all user inputs. Verify that inputs follow specified formats by using validation frameworks and regular expressions.
- Putting Safe Frameworks in Place
Choose security-focused frameworks and libraries. To lessen the likelihood of runtime exploitation, they often include capabilities that automatically manage script handling and data binding, two potentially dangerous actions.
- Ongoing risk assessment
Make sure you frequently do thorough security testing. Discover potential runtime exploitable vulnerabilities using static analysis, which involves inspecting code without executing it, and dynamic analysis, which involves testing and assessing the code while it is running. Another way to keep an eye out for any security vulnerabilities at all times is to use automated testing tools.
- Code Obfuscation
Make it harder for attackers to read and change the app’s code during runtime by using code obfuscation methods.
- Revise and fix library dependencies
Maintain up-to-date frameworks and libraries. Protect yourself from exploitable vulnerabilities by always using the most recent version.
Also read: New Technology Trends 2024